

 Wikipedia Sitemap |
|
|  Useful Links 1 Useful Links 2 |

#1. Be ethical. Be courteous.
#2. Abide by all cyber rules, regulations, and laws wherever they may apply.
#3. Be wary of accepting advice from cyber friends or strangers on the Internet.
#4. Don't flame, spam, spim, phish or vish.
#5. Practise Netiquette.
Netiquette
● Etiquette in technology from Wikipedia, the free encyclopedia.
- "Netiquette, a colloquial portmanteau of network etiquette or Internet etiquette, is a set of social conventions that facilitate interaction over networks, ranging from Usenet and mailing lists to blogs and forums."
- Online etiquette - Digital citizenship is a term that describes how a person should act while using digital technology online and has also been defined as "the ability to participate in society online".
- Cell phone etiquette.
● Netiquette: Social Behaviour by Shing-Ling Sarina Chen, Britannica. Netiquette includes rules that provide guidance for appropriate social interaction and technical performance online.
● What Is Netiquette? (With 10 Basic Rules To Follow) by Indeed Editorial Team, Aug 15, 2024.
● What Is Netiquette? 11 Online Etiquette Rules by Domenic Molinaro, AVG, Oct 15, 2024. Includes: "Netiquette rules for children".
● 15 Rules of Netiquette for Online Discussion Boards [INFOGRAPHIC] by Chana Goldberg, Touro College, May 19, 2014.
● What is Netiquette? 20 Internet Etiquette Rules from Kaspersky. Includes: Netiquette: Safety rules for children.
● Forum Etiquette from Wiki Arch Linux.
#6. Don't accept opinions, rumors, unsubstantiated comments as Gospel truths. Be wary of propaganda and biased information.
#7. Check original and reliable sources to verify accuracy of information whenever possible. Develop a habit to critically evaluate all content on the Internet.
#8. Guard against viruses and hackers, take absolutely NO chances. See ClamWin Free Antivirus, or Anti-Virus or AntiVirus for a free download.
#9. If you have access to an anti-virus program with live update feature, update frequently and have auto-protect running on your computer.
#10. Remember to disable auto-protect before installing new software on your computer if your program does not automatically do it for you.
#11. As a rule, do not send your photo or give personal information to strangers, and do not give passwords or credit card numbers online.
Survival Guide
The paranoid's survival guide, part 1: How to protect your personal data by Robert L. Mitchell, Computerworld, Mar 3, 2014. Privacy is under attack from all quarters, but even today, there are things you can do to protect your personal data. Here are some tips.
● The paranoid's survival guide, part 2: Protect your privacy on social, mobile and more by Robert L. Mitchell, Computerworld, Mar 13, 2014. Here's how to minimize your personal data footprint when messaging, on social media, and using mobile apps.
● The paranoid's survival guide, part 3: Opting out, and how to protect your personal data offline by Robert L. Mitchell, Computerworld, Mar 19, 2014. How to just say no to direct mail and other 'offers'.
● A College Student's Guide to Digital Hygiene, Privacy, and Data Backup by Dmitry Dontov, CEO and Founder, Spin.AI, Jan 6, 2025. The Ultimate Tech Survival Guide for College Students.
● The Definitive Guide to Privacy Online from Privacy Monitor.
Internet users often believe they have no power over companies who collect and sell their personal online data. Learn how to fight back.
● Making mobile payments? Protect yourself from scams by Lisa Lake, Consumer Education Specialist, Federal Trade Commisson (FTC).
1. Never send money to anyone you don't recognize.
2. If you get a cash request from someone you do recognize, call or contact them using a number you know to be right. Confirm they made the request before you send money - even if you've sent them money through the app before.
3. When you use an app for the first time, it will usually ask permission to access information on your device to make payments easier. If you're not comfortable with that, deny access or uninstall the app.
4. Read your bank statements closely and regularly. Ask the app company and your bank to reverse any transactions you didn't authorize.
5. Find out more about mobile payments and secure your mobile device. If you experience a money transfer scam or other fraud, report it to the FTC.
● Tips and Advice on Cyber Security from Federal Trade Commission (FTC).
1. For Consumers: Avoid scams and know your rights. Money & Credit. Jobs & Making Money. Homes & Mortgages. Privacy & Identity. Health & Fitness. Scam Alerts. Hacked Email.
2. For Business: Your link to consumer protection law. Advertising and Marketing. Selected Industries. Credit & Finance. Legal Resources. Privacy & Security. Business Blog. Protecting Small Businesses. Cybersecurity for Small Business.
3. For Military Consumers: Your tool for financial readiness. Homepage. Save & Invest. Earn. Protect. Spend. Blog. Borrow. Scam Alerts. Ways to Avoid Scams.
● Staying cyber safe: 11 top scams and how not to fall for them by
Superaging Staff, SuperAging News Network, 5 Sep 2024.
● Cyber security & fraud prevention learning guide from Canadian Bankers Association (CBA), Sep 22, 2021. Fraud Prevention 101 topics: credit cards, cyber security, debit card, email, fraud, identity theft, joint accounts, malware, passwords, phishing, PINs, Powers of Attorney, privacy, retirement, safety, scams, seniors. Sign up for CBA's free fraud prevention email newsletter to stay ahead of emerging frauds and scams.
● Holiday Cybersecurity Tips from North Carolina Department of Information Technology (NCDIT). Safety Tips for Shopping Online: Use secure Wi-Fi, Lock down your login, Think before you click ... Safety Tips for Giving Online, Safety Tips While Traveling.
Cybersecurity While Traveling.
Cybersecurity While Working Remotely.
Protecting Yourself Against Doxing. Doxing is the act of searching for people's personal information over the internet. The term comes from "document tracing".
● An introduction to cyber security and data protection from University of York, UK. What is cybercrime? Cybersecurity statistics. Common methods cybercriminals use. What are the potential repercussions of an attack?
● The GCA Cybersecurity Toolkit for Individuals from Global Cyber Alliance. Free and effective tools to help protect yourself from cyber risks.
● 11 ways to help protect yourself against cybercrime from Norton.
● How to Stay Safe, Protect Your Privacy and Digital Life from Norton.
What is two-factor authentication (2FA)?
How to help protect your new tech (smartwatches, wearable tech).
Virus warning signs: How to tell if your computer has a virus.
What are Cookies? The purpose of the cookie is to help the website keep track of your visits and activity.
How to remove GPS and other metadata locations from photos.
Dealing with spam text messages and unwanted calls.
What is spyware? And how to remove it.
How to completely wipe a hard drive. You want to donate or recycle your old computer gear, but there's something you have to do first - wipe your hard drive.
And much more.
● 5 sites for fact-checking before you hit "share". Blog by Emma McGowan, Avast, Feb. 1, 2021. Excellent advice to bookmark these sites in your browser.
1. Snopes
2. Breaking News Consumer Handbook: Fake News Edition
3. FactCheck.org: A Project of The Annenberg Public Policy Center of the University of Pennsylvania
4. PolitiFact: Poynter Institute
5. Washington Post Fact Checker. The Truth Behind the Rhetoric by Glenn Kessler
6. Reuters Fact Check
7. Canada Fact Check
8. Canadian and American Fact Checking Sites
9. USA TODAY News Fact Check
10. Google Fact Check Tools
● Avoiding QR code scams. Fraud Prevention from Canadian Bankers Association (CBA), Jun 2, 2022. Sometimes a fraudulent code will lead you to a bogus website site to steal information. Other times, scammers use a QR code to launch a fraudulent payment app or spread malware.
● Security considerations for QR codes ITSAP.00.141M from Government of Canada, Canadian Centre for Cyber Security, Jan 2022. Quick response (QR) codes are small white squares with two dimensional (2D) black markings, similar in look to a barcode. How do QR codes work?
● 16 Jan 2025 - BEWARE OF A RECENT SCAM! Bradford Township Police issue the following warning: A recent scam has been showing up in many states. A "brushing" scam is when someone receives an unexpected gift or item not ordered in the mail from a place like Amazon or other company. Examples of gifts we've seen include rings, bracelets, necklaces, Bluetooth speaker, etc. The gift will have the recipient's address but will not include the sender's information or be from a known retailer.
When the recipient opens the package to see what it is and possibly who sent it, there is a QR code to scan to find out who sent the gift. Once the code is scanned, all the information from that phone will be sent to scammers. They receive all access to the phone. All personal and financial information is accessible to the scammers and often the victim's bank accounts are drained. The gift QR code should NOT be scanned for any reason. QR code scams are nothing new. These scams show up in all places, including parking meters. Inform your family members about the scam and avoid scanning any unknown QR codes included in packages.
● Phishing Quiz from Google. Take the quiz to see if you can tell what is fake. Can you spot when you're being phished?
Identifying phishing can be harder than you think. Phishing is an attempt to trick you into giving up your personal information by pretending to be someone you know.
● How to Avoid Coronavirus Phishing Scams by Bree Fowler, Consumer Reports, March 13, 2020. Watch out for a surge in emails from cybercriminals pitching COVID-19 health information and fake cures.
● How to Keep Yourself Safe From Coronavirus Scams and Fake Health Products by Zee Krstic, Good Housekeeping, Mar 16, 2020. The Secret Service, FBI, and the FTC are warning Americans about scams capitalizing on fear surrounding COVID-19.
● Beware of Robocalls, Texts and Emails Promising COVID-19 Cures or Stimulus Payments by John Waggoner and Andy Markowitz, AARP, Dec 6, 2021. Coronavirus scams spreading as fraudsters follow the headlines. "As of Dec. 2, [2021] the Federal Trade Commission (FTC) had logged nearly 647,000 consumer complaints related to COVID-19 and stimulus payments, 73 percent of them involving fraud or identity theft. These scams have cost consumers $627 million, with a median loss of $400. Criminals are using the full suite of scam tools - phishing emails and texts, bogus social media posts, robocalls, impostor schemes and more - and closely following the headlines, adapting their messages and tactics as new medical and economic issues arise."
● Don't Fall for These 7 Coronavirus Scams by Kailey Hagen, The Motley Fool, Apr 14, 2020. COVID-19 swindles are costing Americans millions. Here's what you need to know to protect yourself. 1. Stimulus check scams. 2. COVID-19 product and treatment scams. 3. Work-from-home scams. 4. Debt reduction scams. 5. A sick family member. 6. Fake websites with exclusive COVID-19 information. 7. Charity scams.
● How to avoid common coronavirus phishing scams from BMO, March 16, 2020. Common COVID-19 phishing scams:
1. Updates from employers: Scammers send emails that appear to come from your employer, with updates about their COVID-19 policies. These emails link to malicious content.
2. Text messages about COVID-19 testing: There have been reports of scammers sending SMS messages that urge the user to click a link for information on how to get tested for COVID-19, or that offer test results. Some request your health card and credit card to schedule an appointment.
3. Government compensation messages: There's been an uptick in fake emails and texts that appear to come from the Government of Canada, offering employment insurance deposits and other government compensation.
4. Medical tips and product offers: Scammers are sending texts and emails offering medical tips for avoiding COVID-19 and information on where to buy medical products, including face masks, online. Example: "Get free surgical masks from the Red Cross" with a link to a fake website.
● Phishing email attack statistics and facts for 2019-2024 by Sam Cook, Data Journalist, Privacy Advocate and Cord-cutting Expert, comparitech, Jan 25, 2024. Phishing attacks remains a huge threat to individuals and businesses. Find out about the latest phishing statistics and facts based on recent studies and reports.
● Those free COVID-19 money offers on WhatsApp and Facebook are scams by Diana Shiller, Investigator, Division of Marketing Practices, FTC, August 28, 2020. "People have reported seeing messages that seem to be from Pepsi, Walmart, Whole Foods, Target, and other big-name brands. These messages all offer money to people who need it - through grants, coupons for food support, or other giveaways. But they're all fake, and not from those companies at all."
● Avoid Coronavirus Scams from FTC. March 2020. Scammers are taking advantage of fears surrounding the Coronavirus.
- Tips: Hang up on robocalls.
- Fact-check information. Know who the seller really is. Check out the seller by searching online for the person or company's name, phone number and email address, plus words like "review," "complaint" or "scam."
- Don't respond to texts and emails about checks from the government.
- Don't click on links from sources you don't know. They could download viruses onto your computer or device.
- Watch for emails claiming to be from the Centers for Disease Control and Prevention (CDC) or experts saying they have information about the virus. For the most up-to-date information about the Coronavirus - COVID-19, visit the Centers for Disease Control and Prevention (CDC) and the World Health Organization (WHO).
- Ignore online offers for vaccinations. Currently, there are no vaccines, pills, potions, lotions, lozenges or other prescription or over-the-counter products available to treat or cure Coronavirus disease 2019 (COVID-19) - online or in stores.
- Do your homework when it comes to donations, whether through charities or crowdfunding sites. If someone wants donations in cash, by gift card, or by wiring money, don't do it.
● Quick tips to spot fake websites and phony retailer apps. Fraud prevention from Canadian Bankers Association (CBA), May 25, 2022. How to protect yourself while shopping online. Site provides clues to help you identify a fake online shopping site, and lists signs of phony apps. Report all shopping scams to your local police department. If you have charges on your credit card that you do not recognize, contact your credit card provider right away.
● Protect yourself from COVID-19 related Phishing scams from Royal Canadian Mounted Police (RCMP). Email Phishing Scams, Common Email Phishing Scams:
(Unemployment scams, Donation scams, Health Care scam), Protect Yourself from Email Phishing Scams, When to Contact the Police.
● FTC: Coronavirus scams, Part 2 by Colleen Tressler, Consumer Education Specialist, FTC, March 19, 2020.
● Tips to help you avoid post-disaster scams by Colleen Tressler, Consumer Education Specialist, FTC, August 26, 2020.
● Online security tips for working from home by Lisa Weintraub Schifferle, Attorney, FTC, Division of Consumer & Business Education, March 18, 2020.
● The lead-generation bait-and-switch by Lisa Lake, Consumer Education Specialist, Federal Trade Commission (FTC), April 12, 2019. "When you search online for jobs, benefits, or government assistance, you want to be sure you wind up where you need to be ... Check out the URL before you click. Search online for that URL, plus the words 'review' or 'complaint.' Do the same thing with the company name, if you can find it. That will tell you what other people have experienced with that site. Look for sites with '.gov' in the URL ... government sites are the safest bet."
● How Much Privacy Do You Have Online? From University of Dayton School of Law, University of Dayton's online JD degree, January 17, 2019. Four Ways to Take Charge of Your Digital Privacy:
1. Know what to look for in the Terms and Conditions.
2. Clear out cookies and fully close a browser after every session.
3. Take advantage of customizable settings.
4. Use digital tools to better understand consumer rights.
● 6 Rules for Smart Online Shopping from Oprah.
● How to spot and avoid fraud while shopping online from TD Bank, Dec 6, 2023.
● 7 Ways to Protect Your Privacy Online by Kara Brandeisky, Money, June 5, 2014.
● Internet privacy from Wikipedia.
● How Privacy Vanishes Online by Steve Lohr, Technology, New York Times, 16 Mar. 2010.
● Security is locking your door. Privacy is closing the blinds. On Data Privacy Day (January 28), Avast offers a tip for keeping peeping Toms out of your life by closing your digital blinds!
Use encrypted messaging apps. Don't want your private messages to friends and family to be intercepted - and read - by someone else? You need an encrypted messaging app (or a VPN). Just search the App Store or Google Play for one of these free apps: Dust, Signal, WhatsApp, or Wickr Me. (If you're an iPhone user, your Messages app already encrypts all of your iMessages out of the box.)
#12. If you must enter your password, give personal information or credit card numbers online, do so cautiously and only if you are sure that the Web site is secure. A
KEY or PADLOCK in yellow or in a yellow box is visible at the bottom of the screen when the site is secure. Note also that in the address or URL, the hypertext transfer protocol "http" will change to "https" indicating that the site is indeed secure. Never shop online without using a secure browser such as Moxilla Firefox, Google Chrome, Opera or Apple Safari. See Shopping and paying safely online from Money Helper.org.uk.
● The Safer Way to Click and Buy from RBC Royal Bank of Canada. Follow these six key tips to keep your personal (and financial) details private. 1. Protect those passwords. 2. Be cautious about convenience. 3. The preferred way to pay. 4. Use apps appropriately. 5. Cross-border shopping. 6. Help your bank help you.
● 14 Tips for Safe Online Shopping by Eric Griffith, PC Magazine, May 18, 2020. Billions of dollars are spent shopping online ever year. While most transactions will be uneventful, security on those purchases is not a given. These tips can help.
● Online Safety Basics: Online Shopping from National Cybersecurity Alliance, StaySafeOnline.org. Online shopping isn't just convenient for us and good for businesses, it's good business for the fraudsters and cybercriminals. Scammers try to trick us into paying for goods we won't receive or obtain our personal information for financial gain. Online Shopping Tips:
Think before you click.
Do your homework and check trusted sources.
Consider your payment options: Using a credit card is much better than using a debit card. There are many services you can use to pay for purchases - like Google Pay, PayPal - without giving the merchant your credit card information directly. You only need to fill out required fields at checkout and you should not save your payment information in your profile. If the account autosaves it, after the purchase go in and delete the stored payment details.
Watch what you give away: Be alert to the kinds of information being collected to complete your transaction.
Keep tabs on your bank and credit card statements: Be sure to continuously check your accounts for any unauthorized activity. Set up alerts so that if your credit card is used, you will receive an email or text message with the transaction details.
Keep a clean machine: Most current versions of software and apps updates protect your devices from new threats or vulnerabilities.
Lock down your login: Create long and unique passphrases for all accounts and use multi-factor authentication (MFA) wherever possible.
Use a secure Wi-Fi: Using public Wi-Fi to shop online while at your favorite coffee shop is convenient, but not cyber safe. Don't make purchases via public Wi-Fi; instead use a Virtual Private Network (VPN) or your mobile phone as a hotspot. Or, save those purchases in your cart for later and wait until you're home and on your own secure network.
● Online Shopping Guides.
#13. If you experience something suspicious online or know something is dreadfully wrong, notify someone you trust immediately.
#14. Read carefully agreements, important notices, terms and conditions, before subscribing, downloading, registering, buying, ordering, or "signing" anything online.
#15. Be very cautious when downloading free software. Some sites provide free download of software but long distance charges may apply for every minute of download. Some sites ask you for your credit card information before free downloads or first 30 days free usage.
#16. Be careful what you say (i.e. type) while you are in a chat room. Don't say anything that you may regret later. What you say could be permanently saved or printed by any party "conversing" with you or "listening" to your conversation online.
#17. Never leave your good personal email address to anyone in a chat room, discussion group, newsgroup, on a bulletin board, or when using an instant message service.
#18. Don't send anything by email, or attach anything to an email that you don't want the WHOLE WORLD to read, see, hear, or know about, now or in the future. It may come back to haunt you when you least expect it. Remember that an email is a written record accessible by anyone, anywhere, at any time, FOREVER! An email and its attachment could be easily stored, printed or redistributed by anyone.
"Be careful what you say in your work email account, or in your company Slack channel, or anywhere a record is kept. You never know when and where it'll come back to haunt you." ~ From article: "The cofounder of Google's Android just proved why you should always be careful what you say in work email" by Matt Weinberger, Business Insider, 12 May 2016.
Safety tips when using social media from TD CanadaTrust:
● Be wary of requests for money from a friend or relative in trouble. Fraudsters sometimes hack into social media accounts and make monetary requests to get unsuspecting victims to wire them money.
● Don't click on links from people you don't know, especially if these were received via a private message. This could lead to the installation of financial malware or other harmful software on your device.
● Don't post sensitive personal information or disclose financial information pertaining to yourself or others through social media. Legitimate businesses should not ask for sensitive information or pressure you into providing it through social media.
● Familiarize yourself with the social media site's privacy settings, which allow you to choose how much personal information you reveal and to whom.
● Limit access to close friends, relatives and coworkers. Spend a moment vetting new requests, ensure you actually know the person or business and want them to see what you post.
Top 10 Scams Targeting Seniors & How to Avoid Them by Sohail, Technology for Seniors (techandsenior.com), 15 Aug 2024.
Passwords
#19. Choose a strong password. Advice from Microsoft: How to create a strong password:
A strong password is one that's difficult for others to determine by guessing or by using automated programs. Do not use single dictionary words, your first or last name, date of birth, or other personal info that can be easily obtained, or a password that contains part of your email address or phone number.
A strong password:
● Is NOT a common word or name, or a close variation on a common word or name.
● Contains 7 to 16 characters.
● Uses at least 3 of the following 4 types of characters:
Uppercase letters (A, B, C)
Lowercase letters (a, b, c)
Numerals (1, 2, 3)
Special characters ( `~ ! @ # $ % ^ & * ( ) _ + - = { } | [ ] \ : " ; ' < > ? , . / )
An easy way to choose a better password for your sensitive online accounts from Canadian Bankers Association (CBA). Use a passphrase instead of a password.
#20. List of the most common passwords from Wikipedia. Top 20 most common passwords according to National Cyber Security Centre (NCSC), Keeper, SplashData, and NordPass. Rank 2021 from NordPass:
1 - 123456
2 - 123456789
3 -12345
4 - qwerty
5 - password
6 - 12345678
7 - 111111
8 - 123123
9 - 1234567890
10 - 1234567
11 - qwerty123
12 - 000000
13 - 1q2w3e
14 - aa12345678
15 - abc123
16 - password1
17 - 1234
18 - qwertyuiop
19 - 123321
20 - password123
● Ranked: The World's Top 100 Worst Passwords by Davey Winder, Senior Contributor, Forbes, Jun 29, 2021. Davey Winder is a veteran cybersecurity writer, hacker and analyst.
● The Worst Passwords in the Last Decade (And New Ones You Shouldn't Use) by CyberGhost Research Team, Dec 9, 2021. 81% of all data security breaches are caused by weak passwords. 60% of people use the same passwords across multiple accounts. 51% of people use the same password for personal and work accounts. Millions of passwords are hacked every year. The most common password in the world is "123456". In 2019, one of the most widely used passwords was "password" occurring in 3.6 million breaches, and "qwerty" was involved in 4 million cybersecurity breaches. This site provides advice on how to create good passwords that are difficult to hack.
#21. Don't use the same password at multiple sites or for all your email accounts. If you have more than one email account, use a different password for each account. Use your own association method to link account with password to help you remember the two. However, you need not worry unduly if you cannot remember your password as most sites will send you an email to assist you with a forgotten password - just don't forget your account, or you may have trouble cancelling the old account to open a new one.
#22. Personal account and financial information are often obtained by scam artists who send unsolicited email to unsuspecting users asking them to "update" their account information. See Cyber Crime - The Cyber Threat from Federal Bureau of Investigation (FBI). Be Careful What You Download: Carelessly downloading e-mail attachments can circumvent even the most vigilant anti-virus software. Never open an e-mail attachment from someone you don't know, and be wary of forwarded attachments from people you do know. They may have unwittingly advanced malicious code. If you are the victim of online or internet-enabled crime, file a report with the Internet Crime Complaint Center (IC3) as soon as possible.
● 3 financial scams and how to spot them by Robyn K. Thompson, Fund Library, March 14, 2019. 1. Fake CRA audit scam. 2. Binary option scam. 3. Locked-In Retirement Account (LIRA) Loan Scam. Also: How to avoid becoming a victim.
● 300+ Terrifying Cybercrime and Cybersecurity Statistics (2024 EDITION) by Andra Zaharia, comparitech, Mar 27, 2024. Reviewed by Paul Bischoff, Tech Writer, Privacy Advocate and VPN Expert.
● Slam the scam - Protect yourself against fraud from Canada Revenue Agency (CRA). Watch Video: Beware of scammers posing as CRA employees. See details on the following topics:
● Examples of fraudulent communications: telephone, letter, emails, text messages, online refund forms.
● Know how to recognize a scam
● How to protect yourself from identity theft
● Report a scam
● What to do if you were scammed?
● Scam stories
● External resources
● Print-ready posters and handout for service providers
● Fraud Prevention Tool Kits from Canadian Bankers Association (CBA).
Email and Web Scams: How to Protect Yourself. Advice from Microsoft.
Top 10 most common Online, Internet and Email scams & frauds from The Windows Club, 1Feb. 2020. Nigerian Scam, International Lottery Scam, Travel Scams, Credit Card Scams, Job Scams, Digital Payment Scams, Online Ad Scams, Investment Scams, Disaster Relief or Rescue Scams, Ask for Help Scams. Site also provides a link for you to Track Scams in USA and Canada from BBB Institute for Marketplace Trust.
RCMP says free trial scams are fraudulent, but credit card companies make victims pay by Tyana Grundig and Greg Sadler, CBC News, Oct 13, 2017. "Every week, Marketplace receives dozens of emails from Canadians telling us about all kinds of consumer concerns and deceptive schemes. Renovation ripoffs. Moving company mishaps ... But there's one scam that has generated more angry emails than all the rest: the not-so-free face cream trial. Marketplace has received hundreds of emails from viewers who've been stung by surprise credit card charges they couldn't get reversed after signing up for what they thought were 'risk-free' product trials ... Both Visa and Mastercard told Marketplace that cardholders will not be charged for fraudulent transactions through their zero liability policies, but unlike the RCMP's anti-fraud unit and the Competition Bureau, they don't seem to consider subscription traps to be fraudulent."
Subscription traps: "no-strings attached" trial offers could leave you with your hands tied from Competition Bureau Canada, Mar. 11, 2020. Tips on how to avoid the free-trial trap. "If you do sign up for a free trial, protect yourself:
● Keep all receipts, emails and text messages.
● Check your credit card statements regularly for unauthorized charges.
● Know that you can contact your financial institution to request a stop payment because of suspected fraud.
● Remember that there is no shame in being the victim of a scam. Report suspected fraud and help the authorities and others like you."
Contact the Competition Bureau and file a complaint by phone at 1-800-348-5358 or online. You can also file a complaint with the Canadian Anti-Fraud Centre (CAFC); the Better Business Bureau or your provincial / territorial consumer protection agency.
Government Imposter Scams. How to Recognize a Government Imposter. Five Ways to Beat a Government Imposter Scam. Report the Scam.
● SSA imposters top IRS in consumer loss reports by Seena Gressin, Attorney, Division of Consumer & Business Education, Federal Trade Commission (FTC), April 12, 2019. "Have you gotten calls about supposed problems with your Social Security number from callers pretending they're with the Social Security Administration (SSA)? If so, you're not alone. Our latest Data Spotlight finds that reports about SSA imposters are surging ... people told us they lost $19 million to SSA imposters in the past year ...
If you get one of these calls, remember - the real SSA will never contact you out of the blue or tell you to put money on a gift card or, ... visit a Bitcoin ATM, or wire money. If your caller ID shows a number that looks like it belongs to the SSA, don't trust the number - scammers fake their caller ID all the time. If you're worried, hang up and call the SSA yourself at 1-800-772-1213. Check out the Data Spotlight for more information. If you think a scammer has your Social Security number, visit IdentityTheft.gov/ssa to learn what you can do."
Message from Social Security Administration (SSA) - https://identitytheft.gov/SSA:
● Government employees will not threaten to take away benefits or ask for money or personal information to protect your Social Security card or benefits.
● Tips for holiday gift card shopping by Cristina Miranda, Federal Trade Commission (FTC), 11 Dec 2019. "Gift cards are a scammer's favorite way to steal people's money. Anyone who demands that you pay them with a gift card, for any reason, is always a scammer. Report gift card scams directly with the card issuer, then report it to the FTC at ftc.gov/complaint."
● Scammers can fake your caller ID. So don't be fooled if the call seems to be from the SSA's real phone number (800) 772-1213 or the SSA Inspector General's Fraud Hotline number.
● If a caller asks for your Social Security number, bank account number or credit card information, hang up.
● Report suspected scams to the SSA Inspector General at (800) 269-0271 or oig.ssa.gov/report. Visit IdentityTheft.gov/SSA for more tips.
Student Loan Scams from Federal Trade Commission (FTC).
The sneakiest new shopping scams: Easy ways to avoid the biggest rip-offs online and in stores from Consumer Reports.
Scams and Fraud from Royal Canadian Mounted Police (RCMP).
Stop Scammers from Targeting Your Teens by Elizabeth Rogers, Zoomer.
Avoid the Latest Hotel Scam by Cynthia Ross Cravit, Zoomer.
How to Report Fraud Co-authored by Scott Nelson, JD, Police Sergeant, Mountain View Police Department, wikiHow, Apr 15, 2021. Fraud is a criminal offense perpetrated when an individual deceives others for financial or personal gain. If you are the victim of fraud, or if you witness fraudulent activity, you should report it immediately.
Find out how to report different types of fraud: Identity Fraud, Internet Fraud , Credit Card Fraud.
Contact the Internal Revenue Service (IRS) to report tax fraud. Go online to IRS.gov and search for Form 3949-A. You can print it out and mail it or submit it online.
Email the Department of Justice to report bankruptcy fraud. Write out a fact-based report that includes your contact information and send it to USTP. Bankruptcy.Fraud@usdoj.gov.
Report stolen or fraudulent checks to the National Check Fraud Service. Call 1-843-571-2143 to report personal check fraud or counterfeit checks.
![]() How to report fraud from Government of Canada. Marriage Fraud, Immigration Fraud, Citizenship Fraud. How do I report Internet, email or telephone scams and fraud? Posters and Tip Sheets.
How to report fraud from Government of Canada. Marriage Fraud, Immigration Fraud, Citizenship Fraud. How do I report Internet, email or telephone scams and fraud? Posters and Tip Sheets.
![]() Report Scams and Frauds in the United States. Common scams and fraud, Census fraud, Food stamp (SNAP) fraud, Financial fraud including credit, loans, and mortgages, Identity theft or data breaches, Immigration fraud, International scams, Internet fraud, Investment fraud, IRS and other government imposter scams, Mail fraud, Medicaid fraud, Medicare fraud, Misuse of federal funds, Moving fraud, Social Security fraud, Telephone scams, Welfare or Temporary Assistance for Needy Families (TANF) fraud, and Report Suspected Tax Fraud to the Internal Revenue Service (IRS).
Report Scams and Frauds in the United States. Common scams and fraud, Census fraud, Food stamp (SNAP) fraud, Financial fraud including credit, loans, and mortgages, Identity theft or data breaches, Immigration fraud, International scams, Internet fraud, Investment fraud, IRS and other government imposter scams, Mail fraud, Medicaid fraud, Medicare fraud, Misuse of federal funds, Moving fraud, Social Security fraud, Telephone scams, Welfare or Temporary Assistance for Needy Families (TANF) fraud, and Report Suspected Tax Fraud to the Internal Revenue Service (IRS).
Reporting fraud not only improves your chances of getting some of it back and avoids future losses, but also helps law enforcement authorities to stop scams before other people become victims. See warning signs of common scams and fraud to protect your personal and financial information.
Guide to Consumer Complaints, Fraud, and Online Shopping Scams from Arrest Records. What are consumer complaints?
Most common types of consumer complaints: 1. Sweepstakes and lotteries. 2. Impostor scam. 3. Internet auctions. 4. Foreign money offers. 5. Internet services. 6. Car sales. 7. Construction work.
What is consumer fraud?
Most common types of consumer fraud: COVID-19 fraud, Identity theft, Upfront fee fraud, Debt elimination fraud, Nigerian fraud, Cashier's check fraud, Bank fraud, Phishing.
Most common online shopping scams: 1. eCommerce Fraud. 2. Online auction fraud. 3. Fake websites.
How to report consumer fraud.
How Scammers Make You Pay by Lois C. Greisman, Federal Trade Commission (FTC), Jan. 4, 2018. Watch a short video. "... nobody legitimate is ever going to say you have to pay by wiring them money, getting iTunes cards, or putting money on a MoneyPak, Vanilla Reload, or Reloadit card."
![]() Protect yourself against fraud from Canada Revenue Agency (CRA).
Protect yourself against fraud from Canada Revenue Agency (CRA).
![]() ● Call 1-866-828-5961 to place a Fraud Alert on your Equifax Credit Score Report.
● Call 1-866-828-5961 to place a Fraud Alert on your Equifax Credit Score Report.
![]() ● Once a year, you can call Equifax at 1-900-465-7166 to get a free Credit Report which will be mailed to your address in 3-5 working days. Be prepared to have needed info ready such as: your SIN, DOB, House Number, Postal Code, etc. In addition, you have an option to pay $11.95 (tax included) with your credit card to get your Credit Score along with your Credit Report.
● Once a year, you can call Equifax at 1-900-465-7166 to get a free Credit Report which will be mailed to your address in 3-5 working days. Be prepared to have needed info ready such as: your SIN, DOB, House Number, Postal Code, etc. In addition, you have an option to pay $11.95 (tax included) with your credit card to get your Credit Score along with your Credit Report.
![]() ● Request to Obtain Your FREE Credit Report from Equifax.
● Request to Obtain Your FREE Credit Report from Equifax.
![]() ● Once a year, you can also call TransUnion of Canada at 1-800-663-9980 to get a free Credit Report.
● Once a year, you can also call TransUnion of Canada at 1-800-663-9980 to get a free Credit Report.
![]() ● Fill Out the Form to Obtain Your TransUnion Credit Report, Score and More
● Fill Out the Form to Obtain Your TransUnion Credit Report, Score and More
According to the Canadian Bankers Association Fraud Prevention: "One example is a scam disguised as a mystery shopping program, where consumers are 'hired' as mystery shoppers and mailed a cheque which they are asked to deposit into their bank account. They are then asked to immediately return part of the funds once the transaction is complete. Because the cheque is fraudulent, it's returned unpaid and the customer would lose the amount sent to the fraudster."
Fraud Prevention: Practice Safe Online Security With These Five Tips by Sarita Harbour, from RBC Royal Bank of Canada, March 1, 2017. 1. Create a Strong Password. 2. Don't Open Email from Unknown Senders. 3. Look for the Lock Icon. 4. Use All Available Security Feature. 5. Steer Clear of Public WiFi.
● Advice from RBC: If you receive a communication from Rogers Bank, the 'from' field and email domain should be recognizably from Rogers Bank (e.g. @rogersbank.com), and website links must always contain: 'https://www.rogersbank.com/'. If you receive a link that does not match this address or includes additional symbols or numbers (e.g. www.rogersbank1.com), please DO NOT click the link, open any attachments, or reply to the email. Please report any suspicious communications to Rogers Bank.
● Security Dangers of Public Wi-Fi. YouTube video, 2:37 min. Published on Jan 24, 2017 by Kaspersky Lab. Know the risks of using free public wi-fi networks. These security tips will help protect your device, as well as your identity and personal data from cybercriminals.
Cyber Hygiene from Canadian Bankers Association. Cyber hygiene is a great way to think about the importance of taking regular steps to proactively protect your connected devices, such as mobile phones, laptops, desktop computers and smart appliances from cyber threats. Here's a primer on the most commons frauds and scams and how you can practice cyber hygiene to protect yourself.
Beware These 7 Facebook Scams by Tim Brookes, Dec. 18, 2019. "Unlike the email spam of the late 90s and early 2000s, Facebook's scams can be harder to spot. They hide in plain sight and recycle old tactics while preying on some of the most trusting members of society."
Terrifying New Facebook Scam from Express.co.uk. FACEBOOK users need to be aware of a terrifying new scam, that could see your social media account 'cloned' in a bid to swindle friends and family out of money.
How to stop third-party apps from using your Facebook data and protect your privacy by Serenity Caldwell and Rene Ritchie, 20 Mar 2018.
On Data Privacy Day (January 28), Avast offers a useful tip: Facebook lets third-party apps abuse your private, personal data and the private, personal data of your friends. To stop it, you have to remove those apps from Facebook. Protect your Facebook data from 3rd-party apps. Here's how:
1. Log in to Facebook
2. Click the downward arrow at the top right of your screen, then click Settings
3. Click the Apps and Websites menu to see which apps/websites you're "Logged in with Facebook"
4. Tick those you'd like to stop sharing data with, and hit the blue Remove button.
5 tips to protect your privacy from Avast Blog.
● 1. Make sure everything is up to date.
● 2. Upgrade your Wi-Fi security.
● 3. Use stronger logins with strong passwords.
● 4. Use 2-factor authentication. Two-factor authentication, or 2FA, adds a second step by sending a code to your phone or requiring the answer to a security question.
● 5. Use a VPN. A virtual private network is your own personal encrypted connection to the internet.
#23. Be diligent in preventing identiy theft. Identity theft and identity fraud from Canadian Anti-Fraud Centre.
Identity Theft Is a Serious Crime - Resources from the U.S. Government. "Identity theft happens when someone steals your personal information and uses it without your permission. It's a serious crime that can wreak havoc with your finances, credit history, and reputation - and can take time, money, and patience to resolve." Be extremely cautious when entering contests online, request free brochures, free recipes, free quotes, respond to surveys, registering products online, etc. Never respond to unsolicited invitations or requests by providing them with your email address, your real name, date of birth, place of birth, social security number (social insurance number SIN in Canada), home address, telephone number, marital status, education level, place of employment, income, driver's license number, height and weight, ethnic or racial background, hobbies, and other pertinent information about you or that of your family members or friends.
Check out A Chronology of Data Breaches for data breach alerts, and ZabaSearch.com or SearchSystems.net to see if detailed personal information about you is already accessible in thousands of free online public record databases by anyone at any time, with an option to obtain Background Checks on you.
Phishing Scams
Phishing Scams and How to Spot Them from Federal Trade Commission (FTC). Phishing (short for password harvesting fishing) is a type of online scam that targets consumers by sending them an e-mail that appears to be from a well-known source - an internet service provider, a bank, or a mortgage company, for example. It asks the consumer to provide personal identifying information. Then a scammer uses the information to open new accounts, or invade the consumer’s existing accounts. See Tips to avoid phishing scams.
● There's Something Phishy Going On by Matthew Braga, Tangerine, Mar. 11, 2021. Jobs that don't exist. Fake online stores. Bitcoin fraud, and more. Here's how to protect yourself from today's top threats.
● Phishing: An introduction from Get Cyber Safe, Government of Canada, 11 Mar. 2020. Phishing is a common tactic that cyber criminals use to steal personal and financial information from you. Phishing messages usually take the form of an email or phone call from a cyber criminal who is pretending to be someone they are not, such as your bank. Different forms of phishing:
Smishing - phishing attempt through SMS (text message),
Spearphishing - a hyper-targeted phishing attempt in which a message is designed to sound like it's coming from a source you know personally,
Whaling - a phishing attempt aimed at a high-profile target such as a senior executive or other high-ranking official in an organization or government department,
Spoofing - involves creating a fake website to get someone to share their personal information.
Dangers of falling for a phishing campaign, and How to protect yourself from phishing campaigns.
Caller ID Spoofing from Federal Communications Commission (FCC), 7 Mar 2022. Avoid Spoofing Scams - Tip Card. Phone scammers often disguise their identity by using illegal spoofing techniques to send false information to your caller ID display. Here are some good ways to avoid being spoofed.
Advice from Canadian Bankers Association, July 2023: "Don't fall for the latest text phishing scam"
● How the scams work
Scammers employ a number of tactics to encourage you to fall for their scams including impersonating a legitimate organization like a bank, government or law enforcement agency, referencing current issues and news, and offering an irresistible opportunity. Scammers are using all of these tactics in this latest text phishing scam impersonating the Canadian Red Cross.
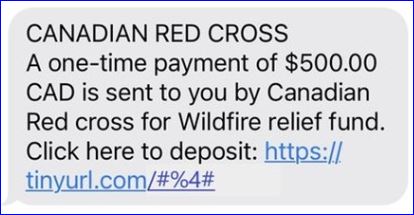
● In this latest scam, according to the Canadian Anti-Fraud Centre, cyber criminals are sending links by text impersonating the Canadian Red Cross and offering money to those affected by recent Canadian wildfires. Clicking on the link will prompt you to provide sensitive personal information such as your banking information, social insurance number or credit card number that the scammers will then use to steal from you.
● The Latest Scams You Need to Be Aware of in 2025 by Louis DeNicola, Dec 20, 2024.
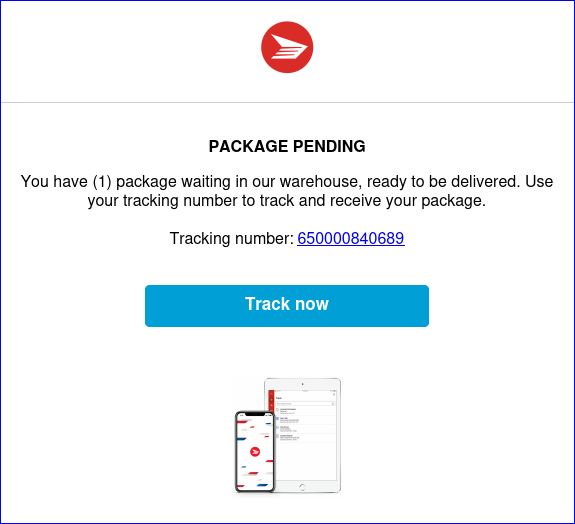
EXAMPLE of an EMAIL FW: AMAZON HAS A SURPRISE FOR YOU Phishing Scam:
TRACK YOUR PACKAGE: #650000840689 <OIOYI@lebarboteur.com>
Sun 2021-02-21 3:35 PM
To: You
This looks like it's from Canada Post, but it's most unlikely that Amazon would authorize Canada Post to send you an email from OIOYI@lebarboteur.com.
If you would like to be removed from our list and stop receiving new event e-mails,
Please Click Here, Or write to:
1217 S. Broadway Ave,Suite 105,,#222,Boise,ID,83706
If you "Click Here", it would take you to a site at i.imgur.com. God knows where that is.
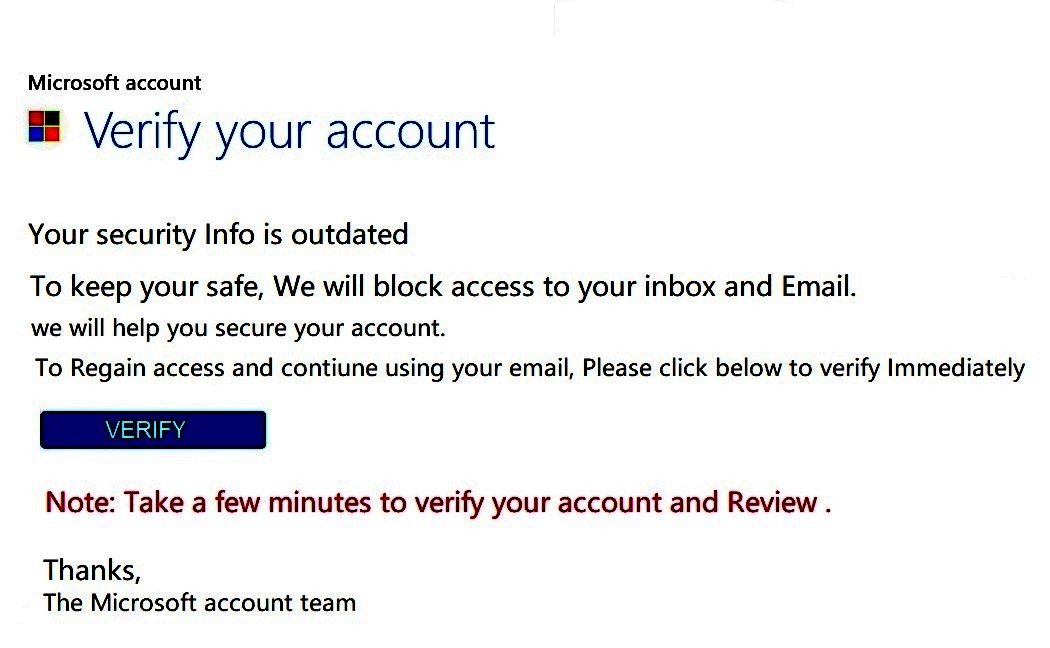
EXAMPLE of an EMAIL NOTIFICATION VERIFY YOUR ACCOUNT Phishing Scam:
EMAIL NOTIFICATION <lui_tszhong@hotmail.com>
Thu 2020-01-30 10:27 AM
mail@services.com
This looks like it's from Microsoft, but it's most unlikely that Microsoft would send you an email from hotmail.com "to keep your safe".
EXAMPLE of a THREAT of EMAIL CLOSURE Phishing Scam:
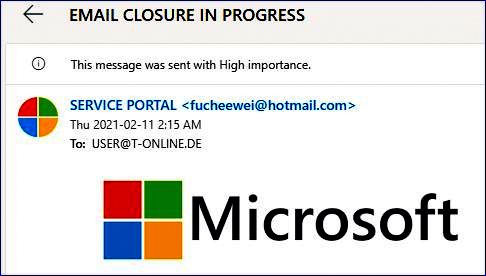
Respected User,
Your Microsoft account is being compromised and new messages will be blocked, Please confirm your account and location to indicate that it is still in use.
Confirm Now
Note: In 24 hours, all Inactive Microsoft accounts will be deactivated.
Microsoft respects your privacy. Read our privacy policy for more information
Microsoft Corporation
One Microsoft Way
Redmond, WA 9805
Always check to see where email is coming from. Microsoft would never send anyone an official email from hotmail.com.
EXAMPLE of a Canada Revenue Agency (CRA) Refund Scam - Email received on April 15, 2020, sent from your email address with your logo!
[Note: This makes it impossible for you to Report to your Email Provider as a Phishing Scam since your own email address is used as the Sender.]
Tax Refund available.

Canada Revenue Agency
Wed 2020-04-15 5:32 PM
Forward More actions
Having trouble viewing this email? View Online
CRA Your Income Tax Reminder April 2020
You are eligible to receive a refund of 520.00 CAD.
You have tax returns for period ending 15 Apr 2019, due 15 Apr 2020, now available for refund!
Remember: We tried to send it to you automatically but were unable to do so as we don't have your details on file.
Ready to refund it now?
Have your credit/debit card ready.
Open the application form below in your browser and login to your myIR account.
Follow the instructions on your screen.
Remember, If you are not the intended recipient of this email, please reply to inform us that you have received this email in error and then delete it without retaining any copy.
Note: Make sure all your income, benefits and family details are up to date in myIR, this will help make sure you're getting the right entitlements.
Your Summary
Issuing number: 8122612218120
Issuing date: April 15, 2020
CRA number: NZ-0113228457NUWH
Payment method: CRA Online
To get Started
Please take few moments to complete this quick refund form.
To start, please visit our website below:
https://www.canada.ca/overpayments/
youremailaddress@hotmail.com
After completing it, please submit the form on your screen and allow us
from 1 up to 5 business days for processing.
------------------------------------------------------------------------------------------------
You may wish to save or print this email confirmation for your records.
------------------------------------------------------------------------------------------------
Sean McBride
The Customer Services Team
Ref: EDM_NOFBT
EXAMPLE of a SURVEY Phishing Scam:
Redeem this 5517!
--Costco Confirmation needed--
<2067office01@siwaaslife.com>
To: maik-andress-@g-mail.com
Fri, Jan 29 at 10:47 AM
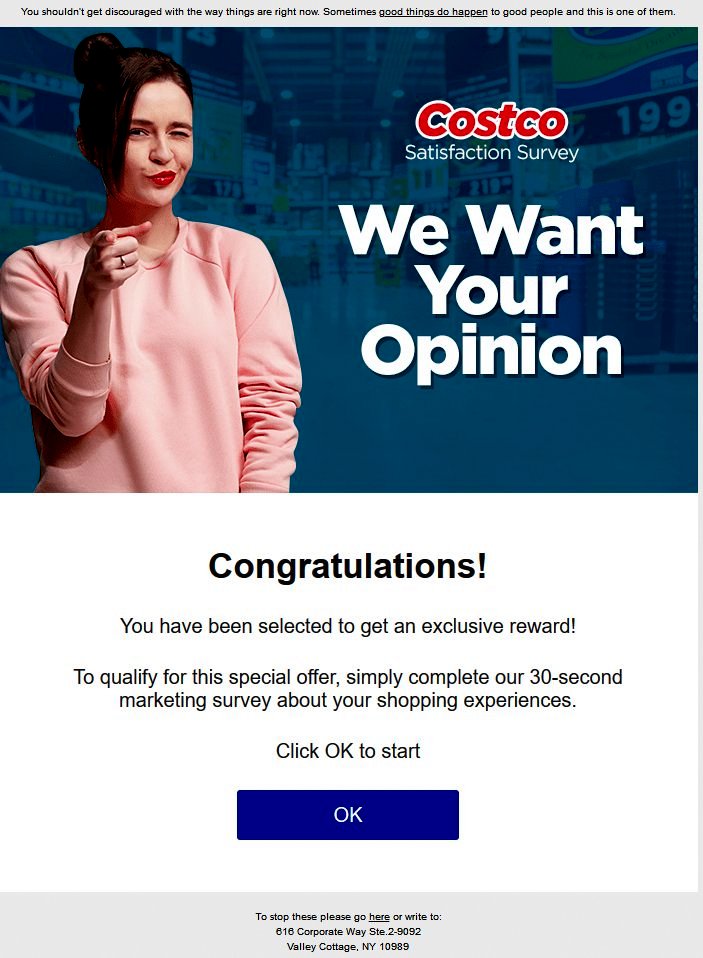
Always check to see where email is coming from. Costco Wholesale would never send you an email from 2067office01@siwaaslife.com and ask you to do a survey. Besides, there is no such website as siwaaslife.com.
EXAMPLE of a Phone Phishing Scam:
Listen to this Telephone Call from Unknown Name Phone number: 1-573-340-4206 regarding your Canadian Social Insurance Number (SIN). Call received on 4 September 2019 at 2:39 pm. "Please do not neglect, this message is from Service Canada ... We're trying to contact you ... been reported severe fraudulent activity with your Social Insurance Number ... Please call us at 1-573-340-4206 immediately to avoid legal issues ..."
(You know, of course, that Service Canada never calls you on the phone to threaten you.)
Online Employment Scams. Advice from Edmonton Police Service. "In 2019, there were 156 employment scam incidents reported to the Edmonton Police Service. There was an overall loss of $525,595.14. Scammers are using advanced tactics to appear legitimate. Scammers use a 'fake maker' to construct a realistic online presence to help sell the scam. They create fake company websites or clone real ones, fake banks with websites, official looking employment documents like offer forms, tax forms, personal information forms, and banking deposit information forms ... The Scam ... Signs a job offer is a scam ... What to do ..."
EXAMPLE of a Job Phishing Scam:
USA.SHOPPER58@sfrbusinessteam.fr
Sat 2019-07-27 9:07 PM
We have an important job offer for you in your location, and
We would like you to participate and complete the assignment.
Once you sign-up, you will be given access to training materials
from our team.
Should you interested, we will pay you $500/ assignment ,
(at least 2 assignments a week will be assigned).
Send your detail below to continued sign up;
- Full Name: _______*
- Full Address: _______*
- State, City, Zip: _______*
- Gender: _______*
- Phone Number: _______*
* Tips and training materials will be provided for free to our
shoppers.
* We will contact you immediately as your application has been
received, thanks!
Regards,
Pammela Foster
MSPA Research 2019.
EXAMPLE of another Job Phishing scam:
"job's solutions services~
sem.nicolet@sogetel.net
To: ms.manager1@aol.com
Cc: sem.nicolet@sogetel.net
Sat 2019-08-24 7:16 PM

Dear Ma/Sir;
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
We have a customer service survey assignment in your location and we will pay $450 / assignment.
Which would come in the form of a cashiers check for you to perform your assignment.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
The job entails an Evaluation process such as visiting Wal-mart/K-mart,e.t.c
Send below information to get started If you are still Interested Applicants are to forward
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
> * name (first/last):
> * address:
> * city, state, & zip code:
> * age, gender:
> * phone:
> * e-mail:
Thank You for Your participation and being here with Us.
Sincerely,
The MS applications team
(C) 2019 SR & I. All rights reserved.
EXAMPLE of yet another Job Phishing scam:
Mystery Shopping
⚑ Flag for follow up.
From: support7@9services.com
Sent: December 7, 2019 11:34 AM
To: raghad_rose@gmx.com
Subject: Mystery Shopping

[Description Jobs]
1. You will be assigned to visit a shop.
2. You need to pretend to be a normal potential "customer" who is looking for a particular service or product.
3. You will then finish an online questionnaire to share with us your customer experience.
[Requirement]
1. 18 Years old or above.
2. Can read and write English.
3. Can speak local language well.
4. No experience needed Like Shopping.
[Job pay]
1. Most of the time you will only need to spend 1 hours on the visit.
2. You will get $500 for each assignment.
Give me your information for register ;
1. Name :___
2 Your Address :___
3. Citys / States / Countrys :___
4. Zip Codes :___
5. Phones :___
6. Ages : .___
7. Gender :___
8. E-Mail :___
Your response would be greatly Appreciated
Kind regards,
Raffaele Spano
MS-Selection (c) 2019.
Even if you need a job badly, don't fall for this type of phishing scam and give strangers your personal information online. $500 for an hour's work sounds unreal. Note the telltale signs of scammers: funny email address from an unknown or nonexistent company "9services.com", and numerous grammatical errors such as incorrect use of capital letters: "Like Shopping, Appreciated" and plurals: "1 hours", info on your "Countrys, Ages", etc.
EXAMPLE of a Donation Phishing scam:
Zihan Shen
Mon 2019-07-29 11:42 AM
Greetings from Atman Foundation.
This is to inform you that we have a donation worth $899,998.00 USD for you, this is due to the conflict around the world right now, and children in places like Syria, South Sudan and Yemen are trapped in violent conflict. They are fleeing from war and disaster in greater numbers than at any time since World War II. And in countries like Nepal and the Philippines, children have seen their houses destroyed by natural disasters such as earthquakes, typhoons and flooding communities. This donation will serve as a great help to the world. You will take 50% of this donation amount, and share the balance 50% to those in need all around the world. contact us with your name, age, country, state, occupation, phone number and city.
Our email: atmanfoundation07@gmail.com
Regards,
Jane B. O'Connell
(President) Altman Foundation
The following Phishing example tempts curious people to reply to find out about a "donation" made to them. (Now, what are the chances that anyone from Mexico would want to donate money to you, a total stranger?)
Re: Good Day
omar.gamez01@cfe.gob.mx
Fri 2019-09-20 12:54 PM
A Private donation has been made to you contact ( bloombergm023@gmail.com ) for more info.....
-----Omar Gamez Vargas/DIS/VMN/CFE@CFE escribió: -----
=======================
Para: omar.gamez@cfe.mx
De: Omar Gamez Vargas/DIS/VMN/CFE@CFE
Fecha: 20/09/2019 06:11
Asunto: Re:
=======================
Hang up on fake "refund calls" by Bridget Small, Consumer Education Specialist, Aug. 27, 2020. Recently, scammers posing as Elite IT agents have been making calls. They say they're giving refunds related to the 2019 case (not true), and urging people to hand over control of their computers (not safe). If you get a call from Elite IT, hang up and report it. It's a scam. When the FTC gives a refund, it never requires you to pay upfront fees, or asks for sensitive information, e.g. Social Security number or bank accounts.
Unexpected prize & lottery scams from Scamwatch.gov.au. Unexpected prize and lottery scams work by asking you to pay some sort of fee in order to claim your prize or winnings from a competition or lottery you never entered. How this scam works. Warning signs. Protect yourself.
EXAMPLE of a Loan Phishing Scam:
Subject: We_have_been_trying_to_reach_you - please _respond!
Wels Fargo Confirmation <fzb0yhkxzc592fkfumpynfw6yh3uur0saifn@propet.outletbonus.net>
To: Your email address
Dec 5 at 2:49 PM
Final-Reminder:_you are_approved for freedom_debt_relief!
CLICK ON SHOWIMAGES FOR LINKS AND IMAGES.
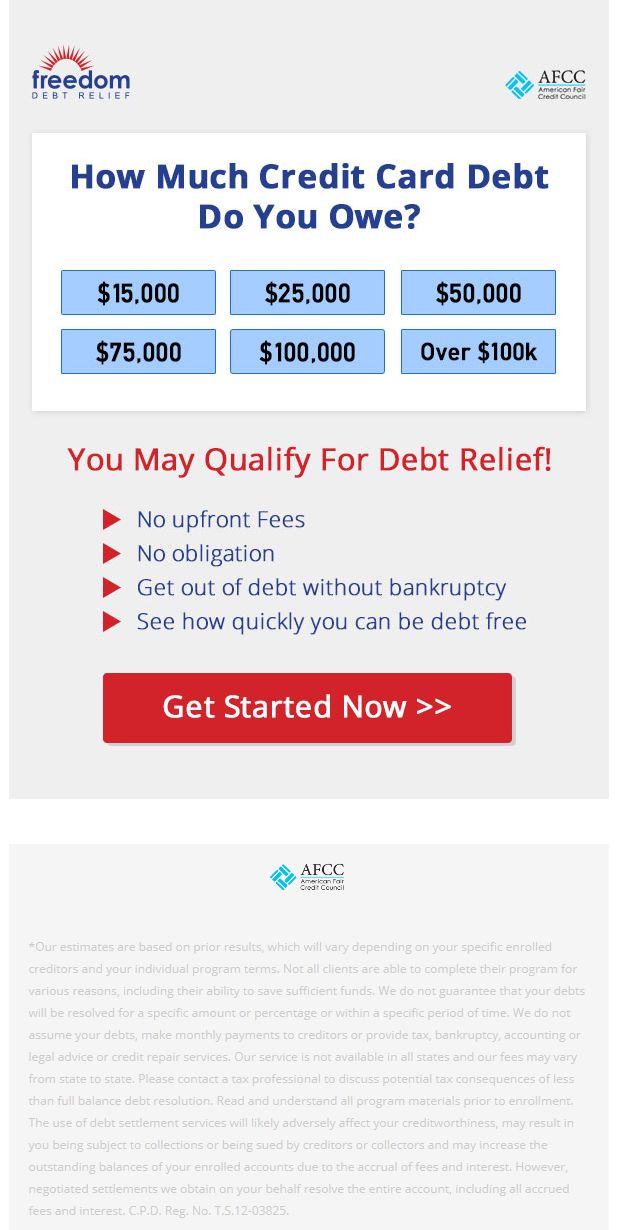
Note: Watch for dead giveaways of scam: funny email address plus spelling of "Wels Fargo" and not "Wells Fargo".
EXAMPLE of a Lottery or Phishing scam:
Received on November 12, 2019, this email was sent to ANJAD (with bcc to me and probably many others) from ANJAD <ayalzubi/87@eng.just.edu.jo> on Tue 2019-11-12 9:22AM
Note: If your name is not in the "To" section of the email, then this phishing email has likely been sent to thousands of people, all in the hopes of snagging a few bites. ~ Info from 10 Common Email & Internet Scams - How to Avoid Them by Jaime A. Heidel.
This Lottery or Phishing scam is easy to spot as it has numerous errors in the use of punctuation marks, spacing between words, no period at the end of a sentence, no comma after "Sincerely", inconsistent use of capital letters, e.g. capital letters for "Full Name, Address", but not for "phone number", as well as wrong use of capital letter for "Sincerely". Are you not suspicious when a stranger from Jordan, in the Middle East, tells you that you have won $1,500,000.00 in the Powerball Lottery Draw from Lottery USA? The sender's email address seems to have come from the Jordan University of Science and Technology.

EXAMPLE of a Bank Phishing scam:
(This banking phishing scam is scary as it looks authentic, complete with an email from "services@americanexpress.com" as well as the official blue American Express logo)
New Update: Online service authentication procedures #RH321
services@americanexpress.com (Email actually came from: <saksidyydtdr01937@presenceamail.com>)
Sat 2019-09-21 7:31pm
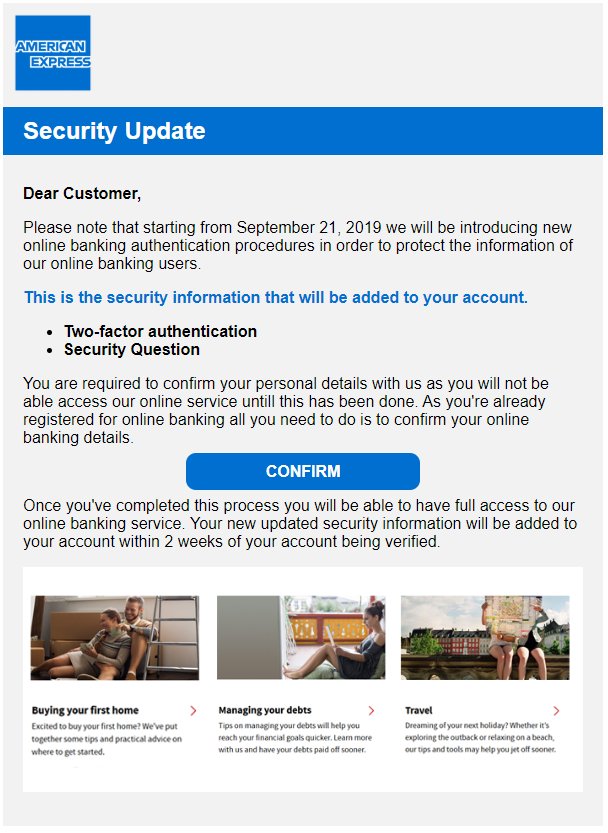
American Express Banking Phishing Scam
received by email Saturday, September 21, 2019 at 7:31pm
EXAMPLE of an Unknown Phishing scam:
URGENT MAIL
Najmi Syahmi Ahmad Fauzy
Fri 2019-10-04 2:33 AM
To: in@officialmail.net
I have urgent business to discuss ?with you, please contact my private Gmail: sandralau216@gmail.com
Thanks.
Tengo asuntos urgentes que discutir con usted, comuníquese con mi Gmail privado: sandralau216@gmail.com
Fraud Prevention Month: Four Ways to Protect Yourself from Phishing Trips and Digital Scams by Sarita Harbour, from RBC Royal Bank of Canada, March 1, 2017. Develop these four online habits to protect yourself from falling victim to cybercriminals: 1. Be Security-Savvy on Social Media. 2. Beware of Online Marketplaces. 3. Think Before You Click!! 4. Malware and Mobile Apps.
A Fraud Expert Is Sharing The Best Tips To Avoid The Latest Phone Scam, And It's Important by Monica Torres, HuffPost Writer, BuzzFeed, 31 Aug 2024. This sneaky, insidious act tricks you into sharing personal information - and it's all too easy for fall for. Here's how to spot it.
How to protect yourself from "phishing" and email scams from BMO Capital Markets. These "phishing" (also called "brand spoofing") emails send you to web sites pretending to be legitimate companies that ask for your personal and financial information. How the scams work. How to identify the scam. How to help protect yourself.
Advice: Always enter your BMO Financial Group web site using your bookmarks or any of BMO's published URLs.
Review your financial statements regularly for unauthorized or suspicious transactions.
Never send personal and/or financial information via unsecured email.
Do not trust email headers. They can be easily forged.
Also from BMO on Privacy and Security: Report Online Fraud (By email, or choose from a list of phone numbers to call),
Protecting Yourself,
Safeguarding Your Computer,
Security Glossary.
Phishing is the most common type of cyber attack. Follow these tips to protect yourself online:
● 1. Think before you click. If you get a strange request, don't recognize the company name, or are asked to open a link or download a file, don't click unless you're sure it's legit.
● 2. Verify the request. If the email sounds urgent or threatening, call the company directly - don't use the number provided in the email, look it up online.
● 3. Watch for popular phishing scams. Fake invoices, files from scanners or printers, email delivery failure messages, and order or travel confirmations are all popular disguises.
Free cruise? Try illegal robocall with an upsell by Amy Hebert, Consumer Education Specialist, Federal Trade Commission (FTC), 10 Jan. 2020. Take a phone survey and get two free tickets to go on a cruise. The call was an illegal robocall. And those free tickets came with a catch.
● 4. Report it. If you receive a suspicious email pretending to be from BMO, forward it as an attachment to online.fraud@bmo.com.
And remember, BMO will never ask for your personal information or account details by email or phone. Reach out to BMO right away if you're concerned about suspicious activity.
Phishing. Articles on Phishing from Avast Blog.
Tips to stay protected from phishing and malware from Dropbox.
DO NOT FALL for any email phishing for your ID and password or asking you to update your banking or credit card info. Remember that your bank or credit card companies NEVER send you unsolicited emails to ask you to update your personal info online. The following is a real phishing attempt with an authentic-looking email from eBay Inc <infos@eBay.erorr.com>, and another from eBay Billing <ebay.security@ebay.intl.com> complete with official eBay logo phishing for important personal information - Subject: eBay New Security Measure!
● - In order to receive uninterrupted service, please update this information.
● - To update your credit/debit card information:
● - Go to http://www.ebay.com/account/MyEbayLogin&verifyinfoID
● - Select My eBay and logon with your eBay User ID and Password
● - Select Use a credit card for automatic payments
● - Update your credit card information following instructions on the next page
Also, your Bank DOES NOT send e-mails:
- Asking you to provide, confirm or update your personal records.
- From a third party address or link to a third party site.
- Asking you to disclose your passwords, PIN#'s, or PVQs (Personal
Verification Questions).
- Containing no information about why you are receiving an e-mail from your Bank.
- Requiring an urgent response from you.
If you provided personal banking information through a link in a phishing e-mail, reset your Online Banking password immediately. If you visited the fraudulent site, clear your browser's cache, then close it and reopen it before accessing your Online Banking again.
See Online Banking Safety Tips from CIBC.
Vishing. What is the purpose of vishing? Why do people engage in vishing? What's the difference between vishing, phishing, and smishing? Vishing examples. What are the signs of vishing? What should you do if you've experienced a vishing attack?
Telemarketing and Unwanted Calls
Vishing - Voice phishing from Wikipedia, the free encyclopedia. "Voice phishing is the criminal practice of using social engineering over the telephone system to gain access to private personal and financial information from the public for the purpose of financial reward. Sometimes referred to as 'Vishing', the term is a combination of 'voice' and 'phishing.'"
Silent call from Wikipedia. A silent call is a telephone call in which the calling party does not speak when the call is answered.
● Silent Calls from TPS Services, UK. Silent calls are generated by diallers. Can silent calls be stopped?
Telemarketing blips: In Canada, a silent call is a telephone call from a telemarketing agency that does not have an agent immediately available to handle the call when you answer. In this instance, the call may be suddenly terminated and you hear silence ("dead air") or you may hear a dial tone from the telephone company indicating the call has been dropped. In the United States, the Federal Trade Commission (FTC) in its regulations for telemarketers, refers to a silent call as an "abandoned call."
How does a silent call work? The majority of silent or abandoned calls are made and caused by automated calling systems known as dialers, or predictive dialers. These dialers, mainly used in call centres, dial telephone numbers automatically and connect people to call centre agents as soon as the phone is answered.
What you can do about silent calls:
● If you are being annoyed by silent calls, or unwanted calls from telemarketers, you can have your number put on the National Do Not Call Registry. This way, your telephone number will not be available to automatic dialers. You can also try blocking individual numbers to avoid specific callers.
● If you are still getting calls, you can complain about any that violate any unsolicited telecommunications rules (this includes automated dialing-announcing device rules). See below on how to file a complaint to Canadian Radio-television and Telecommunications Commission (CRTC).
● The next time you answer the phone and all you hear is silence, don't panic. In fact, don't say anything at all. Just hang up. You've most likely just avoided a pitch from a telemarketer or even better, foiled a possible plan for telephone fraud!
How to Stop Unwanted Calls from Federal Trade Commission (FTC) Consumer Information.
Report Unwanted Calls.
Blocking Unwanted Calls: Scammers can use the internet to make calls from all over the world. They don't care if you're on the National Do Not Call Registry. That's why your best defense against unwanted calls is call blocking.
Robocalls: If you answer the phone and hear a recorded message instead of a live person, it's a robocall. If you're getting a lot of robocalls trying to sell you something, odds are the calls are illegal. Many are also probably scams.
National Do Not Call Registry: The National Do Not Call Registry was created to stop sales calls from real companies. It's free to register your home or mobile phone number.
![]() If you want to stop scammers and telemarketeers, the Canadian Radio-television and Telecommunications Commission (CRTC) suggests that you keep track of the following:
If you want to stop scammers and telemarketeers, the Canadian Radio-television and Telecommunications Commission (CRTC) suggests that you keep track of the following:
1. The telephone number at which you received the telemarketing call.
2. The telephone number and name of the telemarketer that appeared on the ID caller screen or that the person gave you over the phone.
3. The date of the call.
4. The exact time of the call as it appeared on the caller ID screen if you have this feature.
5. Whether the complaint relates to a fax, residential, or business number.
6. Any other information that you have about the call.
7. And then report any call you believe to be fraudulent to the Canadian Anti-Fraud Centre at 1-888-495-8501 or http://www.antifraudcentre.ca." ~ Above information comes from Carol In Your Corner: Scammers Never Rest by CARP.
Sick of annoying calls? 6 ways to block unwanted phone numbers. Whether it's a pushy telemarketer or someone you just don't want to speak to, technology makes it easy to block phone numbers and prevent certain callers from getting through to you. Here are 6 ways to help end those annoying calls.
1. Register on the National Do Not Call List (DNCL)
2. Stop telemarketing calls before they start
3. Enable your smartphone's built-in call blocking features
4. Download a call blocking app on your smartphone
5. Protect your landline with a call blocker
6. File a formal complaint with the CRTC
How to File a Complaint Against Telemarketers and Robocalls from Consumer Fraud Reporting.
The point of caller ID is to allow us to identify who is calling and if we wish to speak to that person. However, some sly telemarketers will mask or falsify the caller ID by using a practice called "spoofing", a strong indication the call may not be legitimate.
A spoofed number can appear as a string of digits (e.g., 000-000-0000 or 123-456-7890), a random number, another company or someone's actual number ... If you receive a telemarketing call you believe has a spoofed caller ID, or keep getting unwanted calls, by law you're entitled to file a complaint.
4 key steps to file a formal complaint to the CRTC against an aggressive telemarketer:
1. Register your number with the National Do Not Call List (DNCL) - Some are exempt from the DNCL rules including telemarketing calls made by, or on behalf of: Canadian registered charities, Political parties, riding associations and candidates, and Newspapers of general circulation for the purpose of soliciting subscriptions.
2. Answer your phone to gather information that CRTC could use against people or companies that don't comply with the DNCL guidelines.
3. Collect details of your conversation with the telemarketer:
Phone number that received the telemarketing call
Name of the telemarketer that appeared on the caller ID screen or that the person on the phone gave you
Date of the call
Exact time of the call as it appeared on the caller ID screen
Any other information you have that relates to the call.
4. Report the incident as soon as possible. After you have this information, you can file a complaint in one of several ways:
Online through the National DNCL website.
By phone (toll-free) at 1-866-580-DNCL (1-866-580-3625).
If you are calling from a TTY device at 1-888-DNCL-TTY (1-888-362-5889).
The sooner you report the incident, the better. Generally, the details will be fresher in your mind and the trail for investigators will still be warm.
To formally file a complaint about fraudulent calls or a spoofing incident, you can contact the Canadian Anti-Fraud Centre at 1-888-495-8501.
![]() Telemarketing and Unwanted Calls from Canadian Radio-television and Telecommunications Commission (CRTC). "If you live in Canada, you can choose to reduce the number of telemarketing calls you receive by registering your residential, wireless, fax or VoIP telephone number on the National Do Not Call Lis (DNCL)." After successfully registering your phone number with DNCL, you will get this message:
Telemarketing and Unwanted Calls from Canadian Radio-television and Telecommunications Commission (CRTC). "If you live in Canada, you can choose to reduce the number of telemarketing calls you receive by registering your residential, wireless, fax or VoIP telephone number on the National Do Not Call Lis (DNCL)." After successfully registering your phone number with DNCL, you will get this message:
"Do not expect calls to stop immediately. Telemarketers have up to 31 days to update their lists and to make sure they do not call you. You could still receive calls within those first 31 days. Registering on the National Do Not Call List (DNCL) will not eliminate all telemarketing calls. There are exemptions within the Rules that may allow calls from organizations such as charities, those with whom you have existing business relationships, political parties and newspapers. You can further reduce unwanted telemarketing calls by asking these organizations to place your number(s) on their own do not call list."
Do Not Call registrations don't expire by Amy Hebert, Consumer Education Specialist, Federal Trade Commission (FTC), Jan. 26, 2018.
Ask Stacy: How Can I Stop Robocalls, Junk Mail and Spam? Article by Stacy Johnson, Money Talks News, August 19, 2016. "The bad news: There's no way to completely eliminate junk calls, mail and email. The good news: You can slow the flood to a trickle in a matter of minutes. Here's how." Article includes: How to Stop Robocalls: Android Robocall Blocking, BlackBerry Robocall Blocking, iOS Robocall Blocking, Windows Robocall Blocking. Some links provided in this article work for residents in the United States only.
Ask Stacy: How Can I Stop These Darn Robocalls? From Money Talks News, January 17, 2018. "More than 2 billion times each month, an American gets an unsolicited, illegal robocall. Here's how to make them stop."
Silence a Ringing Phone (Infographic). How your complaints helps the CRTC bring National Do Not Call List (DNCL) violators into compliance:
1. Register your number - Online: www.lnnte-dncl.gc.ca. By phone: 1-866-580-DNCL (3625). Via TTY: 1-888-DNCL-TTY (362-5889).
2. Answer the call - Even if you're sure it's a telemarketer.
3. Collect the data - Get Telemarketer's name and number, Date and time of call, Your telephone number, Confirmation of solicitation
4. File the complaint - Online: www.lnnte-dncl.gc.ca. By phone: 1-866-580-DNCL (3625). Via TTY: 1-888-DNCL-TTY (362-5889).
CRTC will investigate - To confirm a violation has occurred
CRTC will act - To bring violators into compliance.
Stop Unwanted Calls and Texts from the Federal Communications Commission (FCC). The FCC regulates interstate and international communications by radio, television, wire, satellite, and cable in all 50 states, the District of Columbia and U.S. territories. Contents include: Robocalls, Call Blocking Resources, Spoofing, 'Do Not Call' List, Spam, File a Complaint, Download Consumer Education Materials.
10 Things You Can Do to Avoid Fraud from Federal Trade Commission Consumer Information. Spot imposters, Do online searches, Don't believe your caller ID, Don't pay upfront for a promise, Consider how you pay - "Wiring money through services like Western Union or MoneyGram is risky because it's nearly impossible to get your money back." Talk to someone, Hang up on robocalls, Be skeptical about free trial offers, Don't deposit a check and wire money back, Sign up for free scam alerts from the FTC at ftc.gov/scams.
What you can do to fend off hackers by Alvaro Puig, Consumer Education Specialist, Federal Trade Commission (FTC), 28 Oct 2019.
1. Protect your cell phone - Set your cell phone or smartphone to lock automatically and create a passcode to unlock it.
How to Protect Your Phone and the Data on It.
2. Protect your computer from threats like malware. Use security software and update it regularly. Computer Security. Malware.
3. Connect safely - Know what makes a wireless network secure. Find out how to use public Wi-Fi safely. Tips for Using Public Wi-Fi Networks.
4. Keep your info to yourself - Recognize scammers' attempts to steal your personal information. Phishing attacks by email or text may try to trick you into giving up your passwords, account numbers, or other personal information. How to Recognize and Avoid Phishing Scams.
Is that text message about your FedEx package really a scam? By Alvaro Puig, Consumer Education Specialist, FTC, Feb. 20, 2020. Scammers send a text message with a fake shipment tracking code and a link to update your delivery preferences. Tip: If you get an unexpected text message, don't click on any links. If you think it could be legit, contact the company using a website or phone number you know is real. Don't use the information in the text message.
Hacking
What is hacking? By Matthew Kosinski, Enterprise Technology Writer, IBM, Oct 16, 2024. Hacking (also called cyber hacking) is the use of unconventional or illicit means to gain unauthorized access to a digital device, computer system or computer network.
What is a hacker? From Malwarebytes, circa 2024. Who are hackers? What is hacking? Hacking tools: How do hackers hack? Types of hacking/hackers. Ethical hacking? White, black, and grey hats. (What are 3 types of hacking? Hackers usually fall into three types: black hat hackers, white hat hackers, and gray hat hackers. These are as you can guess are associated with ethical hacking, unethical hacking or something in between.) Hacking prevention. Hacking on Android phones. Hacking on Macs. How does hacking affect my business?
How to Stop a Hacker by Tech Talker Eric Escobar, Scientific American, May 4, 2026.
6 easy tips to avoid hackers by The Sherweb Team, Sherweb.com, Oct 6, 2023.
Internet safety: How to protect yourself from hackers from Chubb.
Stay Safe From Hackers: Protecting Your Accounts & Devices by Chiara Corsaro and Nicole Levine, MFA, Wikihow.com, Jul 22, 2024.
How to Minimize Your Risk of Smartphone Hacking from Privacy Rights Clearinghouse, Posted June 24, 2016.
10 tips to protect against an email hack from Avast Blog.
● 1. Use a password manager and two-factor authentication (2FA) wherever possible.
● 2. If signing up for a new email service, check for 2FA support.
● 3. Don't click links in email or texts .
● 4. Use a VPN on your computer and your phone.
● 5. Don't use public Wi-Fi or public computers, if you can help it.
● 6. Get a strong antivirus.
● 7. Secure your router and Wi-Fi. Ensure you change the admin password for your router and set your Wi-Fi password to something really strong that a hacker could not crack.
● 8. Keep your computer and smartphone OS up-to-date.
● 9. Keep all of your computer and smartphone apps regularly updated.
● 10. Consider putting a credit freeze on your account.
Hacking the World - Hacking Basics by PIA Research Team, Private Internet Access, Oct 4, 2021. Cybersecurity Glossary, General Statistics, Hacking 101.
12 Signs Your Computer Has Been Hacked. YouTube video, 9:31 min. Published on Oct 3, 2017 by BRIGHT SIDE. There are important signs your computer has been hacked and your data has been stolen. Learn the easiest ways to protect your computer from hackers.
![]() Free credit freezes from Federal Trade Commission (FTC) Consumer Information.
Free credit freezes from Federal Trade Commission (FTC) Consumer Information.
"Security freezes, also known as credit freezes, restrict access to your credit file, making it harder for identity thieves to open new accounts in your name. Starting September 21, 2018, you can freeze and unfreeze your credit file for free. You also can get a free freeze for your children who are under 16. And if you are someone's guardian, conservator or have a valid power of attorney, you can get a free freeze for that person, too.
How will these freezes work? Contact all three of the nationwide credit reporting agencies - Equifax, Experian, and
Don't confuse freezes with locks. They work in a similar way, but locks may have monthly fees. If you want a free freeze guaranteed by federal law, then opt for a freeze, not a lock."
![]() 7 tips for staying safe on the web from Google. See also other safety related issues: Phishing, Malware, Secure sites, Safe networks, Mobile security, Check your Gmail account, Family safety, Shopping safety, Locking your screen, Passwords, and Google's security tools.
7 tips for staying safe on the web from Google. See also other safety related issues: Phishing, Malware, Secure sites, Safe networks, Mobile security, Check your Gmail account, Family safety, Shopping safety, Locking your screen, Passwords, and Google's security tools.
![]() How to Prevent Identity Theft from Elite Personal Finance.
How to Prevent Identity Theft from Elite Personal Finance.
![]() Beware of check fraud: Counterfeit cashier's check scams are alive and well. Consumer Reports, 7 March 2014.
Beware of check fraud: Counterfeit cashier's check scams are alive and well. Consumer Reports, 7 March 2014.
![]() Cashier's Check Fraud & Scams: How to Spot a Fake by John S Kiernan, Managing Editor, WalletHub, Dec 8, 2020.
Cashier's Check Fraud & Scams: How to Spot a Fake by John S Kiernan, Managing Editor, WalletHub, Dec 8, 2020.
![]() Client Identity Theft Checklist: Action Steps for Recovery from Payan & Payan CPAs, 2017.
Client Identity Theft Checklist: Action Steps for Recovery from Payan & Payan CPAs, 2017.
![]() Escrow.com. Protects Online Buyers and Sellers from Fraud. For Buyers: Receive merchandise before the Seller is paid. For Sellers: Protect yourself from credit card and payment fraud.
Escrow.com. Protects Online Buyers and Sellers from Fraud. For Buyers: Receive merchandise before the Seller is paid. For Sellers: Protect yourself from credit card and payment fraud.
![]() Fact Sheet: How to Protect Yourself from Identity Theft after a Data Breach from California State Senate, Senator Debra Bowen. Find out what you should do if you become a victim.
Fact Sheet: How to Protect Yourself from Identity Theft after a Data Breach from California State Senate, Senator Debra Bowen. Find out what you should do if you become a victim.
![]() What is identity theft? From TransUnion. What should I do if I'm victim of credit fraud? What are some tips for avoiding fraud? Learn how TransUnion can help you if you are a victim of fraud or read tips on how to avoid becoming a victim of fraud. Fraud Victims Resources - Tips on how to avoid becoming a victim of fraud.
What is identity theft? From TransUnion. What should I do if I'm victim of credit fraud? What are some tips for avoiding fraud? Learn how TransUnion can help you if you are a victim of fraud or read tips on how to avoid becoming a victim of fraud. Fraud Victims Resources - Tips on how to avoid becoming a victim of fraud.
![]() How to Protect Yourself from Identity Theft from Canada Post.
How to Protect Yourself from Identity Theft from Canada Post.
![]() How to recognize phishing e-mails by Elinor Mills, News CNET.
How to recognize phishing e-mails by Elinor Mills, News CNET.
![]() Top 10 Tips for Identity Theft Protection by Rob Bonta, Attorney General, State of California Department of Justice.
Top 10 Tips for Identity Theft Protection by Rob Bonta, Attorney General, State of California Department of Justice.
![]() Report Identity Theft and Get a Recovery Plan from FTC.
Report Identity Theft and Get a Recovery Plan from FTC.
![]() Identity Theft Recovery Steps from True Identity, Mar 7, 2022.
Identity Theft Recovery Steps from True Identity, Mar 7, 2022.
![]() ID Theft from U.S. Norton
ID Theft from U.S. Norton
![]() Identity Theft and Fraud from Canadian Anti-Fraud Centre Identity theft refers to criminals stealing someone else's personal information for criminal purposes. Identity fraud happens when criminals use stolen personal information. It is often used to commit another crime. Actions you can take to protect yourself.
Identity Theft and Fraud from Canadian Anti-Fraud Centre Identity theft refers to criminals stealing someone else's personal information for criminal purposes. Identity fraud happens when criminals use stolen personal information. It is often used to commit another crime. Actions you can take to protect yourself.
![]() Identity Theft Checklist from U.S. Department of Justice. According to a survey by the Federal Trade Commission, ID Theft is the fastest growing crime in America - over 9 million victims per year.
Identity Theft Checklist from U.S. Department of Justice. According to a survey by the Federal Trade Commission, ID Theft is the fastest growing crime in America - over 9 million victims per year.
![]() Identity Theft Protection Quiz from TD Bank.
Identity Theft Protection Quiz from TD Bank.
![]() How-to guide: What to do if your identity is stolen - 5 steps to take immediately from US Bank, 24 Feb 2023.
How-to guide: What to do if your identity is stolen - 5 steps to take immediately from US Bank, 24 Feb 2023.
![]() Three Immediate Steps to Repair Identity Theft as Advised by the FTC from Nisivoccia.
Three Immediate Steps to Repair Identity Theft as Advised by the FTC from Nisivoccia.
1. Place a Fraud Alert. Contact one credit reporting company: Equifax (USA), Equifax (Canada), Experian, Transunion (USA), or Transunion (Canada).
2. Order Your Credit Reports. After the initial fraud alert is placed, order your credit reports from each of the three reporting agencies.
3. Create an Identity Theft Report. An Identity Theft Report will help you deal with credit reporting companies, debt collectors, and businesses that gave the identity thief credit or opened new accounts in your name. Submit a report about the theft to the FTC using this online form.
![]() Internet Fraud, Common Fraud Scams, Internet Scams, Frauds Targeting Senior Citizens from Federal Bureau of Investigation (FBI).
Internet Fraud, Common Fraud Scams, Internet Scams, Frauds Targeting Senior Citizens from Federal Bureau of Investigation (FBI).
![]() A Phew Phishing Phacts. Blog - Datababe's Doodlings or Natterings of a Nerd.
A Phew Phishing Phacts. Blog - Datababe's Doodlings or Natterings of a Nerd.
![]() Protecting Yourself Against Identity Theft: Putting the Freeze on Identity Theft by Suze Orman.
Protecting Yourself Against Identity Theft: Putting the Freeze on Identity Theft by Suze Orman.
![]() Reducing Your Risk of Identity Theft from Privacy Rights Clearinghouse.
Reducing Your Risk of Identity Theft from Privacy Rights Clearinghouse.
![]() Scams by Medium Anti-Fraud Centre.
Scams by Medium Anti-Fraud Centre.
![]() Spear Phishing from Canadian Anti-Fraud Centre.
Spear Phishing from Canadian Anti-Fraud Centre.
![]() Time to Wrap Your Key Fob in Tin Foil by Anthony Alaniz, Jan 2, 2019.
Time to Wrap Your Key Fob in Tin Foil by Anthony Alaniz, Jan 2, 2019.
![]() Top 4 scams identity thieves love. Video from Yahoo, 3:11 min.
Top 4 scams identity thieves love. Video from Yahoo, 3:11 min.
![]() Top 10 Best Anti Phishing Software 2019 from Antivirus Software Guide.
Top 10 Best Anti Phishing Software 2019 from Antivirus Software Guide.
![]() Top Ten Phishing Facts by Lisa Phifer, 12 Apr 2010.
Top Ten Phishing Facts by Lisa Phifer, 12 Apr 2010.
![]() What Are Identity Theft and Identity Fraud? What are the Most Common Ways That Identity Theft
or Fraud can happen to you? From United States Department of Justice.
What Are Identity Theft and Identity Fraud? What are the Most Common Ways That Identity Theft
or Fraud can happen to you? From United States Department of Justice.
![]() Why you might want to wrap your car fob in foil by Phoebe Wall Howard, Detroit Free Press, July 6, 2018, Updated Jan 1, 2019.
Why you might want to wrap your car fob in foil by Phoebe Wall Howard, Detroit Free Press, July 6, 2018, Updated Jan 1, 2019.
![]() Canadian Anti-Fraud Centre (CAFC) from Government of Canada. Recognize it. Report it. Stop it. (Formerly Project PhoneBusters). The CAFC is the central agency in Canada that collects information and criminal intelligence on mass marketing fraud (telemarketing), advance fee fraud letters (e.g. West African), internet fraud and I.D theft complaints. If you live in the Peel Region and you are a victim of a serious scam, you may wish to call the Peel Regional Police at 905-453-2121 or the Canadian Anti-Fraud Centre at 1-888-495-8501.
Canadian Anti-Fraud Centre (CAFC) from Government of Canada. Recognize it. Report it. Stop it. (Formerly Project PhoneBusters). The CAFC is the central agency in Canada that collects information and criminal intelligence on mass marketing fraud (telemarketing), advance fee fraud letters (e.g. West African), internet fraud and I.D theft complaints. If you live in the Peel Region and you are a victim of a serious scam, you may wish to call the Peel Regional Police at 905-453-2121 or the Canadian Anti-Fraud Centre at 1-888-495-8501.
Disposing of Records Containing Personal Information from Privacy Rights, Jul 15 2019. Almost everyone has records containing personal information (Social Security number, financial information, medical history, etc.) around their home. You can help protect yourself from identity theft by properly destroying your old paper and digital records when you no longer need them. Shred Paper Records, Destroy Digital Records: Computer, Phone/Tablet, Portable Storage, Cloud/Remote Storage.
● Reducing Your Risk of Identity Theft from Privacy Rights, Jul 15 2019. Others can get your personal information in many ways including: data breaches, discarded documents, stolen wallets/purses, stolen mail, phishing. Limit, Watch, and Protect Your Cards,Make Better Passwords (and Secure Them), Protect Your Social Security Number, Be Responsible with Your Documents.
Don't Become a Target: Make Smart Choices to Protect Your Privacy from Privacy Rights Clearinghouse, Jan 27, 2014. Monitor your financial accounts, Credit cards are better than debit cards - Always, Watch out for fraudsters, Never give sensitive information out to anyone who calls you, Watch for fraudulent emails, Keep up with your credit reports.
Getting your credit report (United States) by Lisa Weintraub Schifferle, Attorney, Federal Trade Commission (FTC), Division of Consumer & Business Education, 14 Jan 2020.
In the U.S., you are entitled to one FREE credit report per year from each of the three credit bureaus. Only do this through the official site: Annual Credit Report.com.
Starting in 2020, everyone in the U.S. can get six free credit reports a year through 2026 at the Equifax website or by calling 1-866-349-5191. The six credit reports are in addition to the one free Equifax report you can get at www.AnnualCreditReport.com. ~ Info from: Fraud alerts & credit freezes: What's the difference? By Lisa Weintraub Schifferle, Attorney, Division of Consumer & Business Education,
FTC, 13 Feb. 2020.
![]() In Canada, your free credit report is called a "credit file disclosure" by Equifax Canada and a "consumer disclosure" by TransUnion Canada. It does not include your credit score. You can order your credit report FREE of charge once per year by mail, fax or telephone, and you must receive it by mail or in person. If you choose to access it online, you will have to pay a fee.
In Canada, your free credit report is called a "credit file disclosure" by Equifax Canada and a "consumer disclosure" by TransUnion Canada. It does not include your credit score. You can order your credit report FREE of charge once per year by mail, fax or telephone, and you must receive it by mail or in person. If you choose to access it online, you will have to pay a fee.
You can order one report once a year from each bureau free of charge.
Equifax Canada phone: 1-800-465-7166.
TransUnion Canada phone: 1-800-663-9980. Have required info handy when you call: SIN, credit card, DOB, house number, postal code, home phone, bank info, employer, etc. See How to order your credit report from Government of Canada.
The Internet Crime Complaint Center (IC3) is co-sponsored by the Federal Bureau of Investigation (FBI) and the National White Collar Crime Center (NW3C). Filing a Complaint with the IC3. The IC3 accepts online Internet crime complaints from either the actual victim or from a third party to the complainant. Complaints filed via this web site are processed and may be referred to law enforcement/regulatory agencies for possible investigation.
#24. How can you tell if the email originates from a legitimate source? Check the HTML code to see where the link really goes and check the detailed headers to see where the email is coming from. If you are suspicious that the email address is not a real one and cannot be tracked, don't reply to that email, but go directly to the company's URL, then type in the company's good email address to send your reply. See Spoof (Fake) Emails Tutorial from eBay.
#25. Be sure the email address of your recipient is correct. If the user name is unknown, your email will not be delivered and you will receive an error message from the Mail Delivery System. If you have the wrong user name but it exists, you may be sending your email to a total stranger somewhere in cyberspace.
#26. Before rushing off an email composed in anger or frustration, send it to yourself first. If you still feel the same way in 24 hours and have no regrets, forward a gentler, modified version to your intended recipient.
#27. NEVER open an email attachment with the extension .exe .EXE (Executable file), or .jpg .JPG, .jpeg .JPEG (commonly used graphics file
format) or .wmf .WMF (Windows Meta File) no matter how trusted the source without first scanning it with updated anti-virus and anti-spyware software. Don't go by what you see in the surface header because the usual, familiar-looking email address may be disguised and not be genuine. Be sure to check the detailed
email headers to verify that the email originates from a legitimate source. Please note this word of caution from Brent Chivers: Spam and viruses routinely forge the sender address, so the true origin of a message is often not what the visible headers show.
(Received Nov 13, 2013) Info re: CryptoLocker. CyrptoLocker is a malicious program known as ransomware. This type of malware usually stops you from using your computer until you pay a certain amount of money (ransom).
The most common infection vectors for CryptoLocker are spear-phishing e-mails with malicious attachments. The attachment is usually a zip file containing a PDF file which, when opened, executes CryptoLocker.
An ounce of prevention is worth a pound of cure. Here are a few ways that you can protect yourself:
If you receive an unexpected e-mail containing a link you do one or all of the following:
a) Hover your mouse pointer over the link BUT DO NOT CLICK. Look at the address within the link. If it is not what you are expecting to see, don't click it!
b) Contact the sender to verify the validity of the email
c) DELETE IT!
#28. Never respond to email messages that ask you to dial a certain unknown phone number. Some area codes such as 473 or 900 could cost you a bundle.
#29. To avoid sending attachments that may contain viruses to friends, do not send a Web page link as an attachment, copy the URL and paste it into the text of your email.
#30. Don't subscribe to any email that you don't absolutely need. Often when you enter a contest to win something, you are not only giving away your name, address and phone number, you may be subscribing to newsletters and soliciting ads by giving away your email address to numerous other unknown businesses. You will likely be flooded with spam mail shortly after entering the contest.
#31. Unsubscribe (or block) all unwanted email subscriptions that you are currently receiving, but be wary of the sites from which you are unsubscribing. One trick is to ask you to unsubscribe by carefully entering your email address. Your correct and confirmed email address may then be sold or passed on to others without your permission or knowledge.
#32. Never click on any suspicious junk email out of curiosity as that will constitute a response, and a response is a confirmation to the sender that this is your correct email address. You are asking the sender to please spam you some more, and do sell this live, accurate and updated email address to someone else without your permission. Find out - Email Address Harvesting: How do spammers gather private email addresses? By Param Chahal, Template Toaster, Nov 16, 2023. Prevent Email Harvesting. Nov 16, 2023 Dojo's advice: Best way to prevent Email Address Harvesting is to use Contact Form on your website and never put your email anywhere publicly.
How Spammers Harvest Email Addresses - And What You Can Do About It from Expert IT.co.uk, Aug 15, 2019.
DO NOT respond to unsolicited email such as this: "Please forward this to everyone you know ..." for any reason. If you did, you will likely be adding email addresses of your friends and relatives to spammers, passing on any virus contained in links in the original email, as well as adding unnecessary clutter to the Internet.
#33. Use the BLOCK SENDER feature to stop annoying e-mail coming from sources that won't allow you to unsubscribe or e-mail addresses that do not really exist and you cannot get rid of.
#34. Use the FILTER feature to send unwanted in-coming email directly to TRASH and not to your INBOX. You may wish to open a Gmail account (free email from Google). You will get less spam as junk email is not sent directly to your INBOX with gmail.com. If you do get anything in the spam folder, gmail will tell you how many there are, and you can quickly delete all spam email messages without reading any of them by clicking on "Delete all spam messages now". Of course, you have an option to read or move them, or to "Delete Forever" as you wish.
#35. Do not mix the use of your good personal email account with the use of a junk email account. Guard your personal account by not giving your email address to just anyone. Open a free junk email account for use with the public, to register for access to Web sites, to participate in forums, to enter contests, to request coupons, to get free estimates, to ask questions or submit comments to banks or other institutions, to receive potentially useless, annoying, or obnoxious email, etc.
#36. Empty BULK mail and TRASH frequently if they are not automatically removed. All of the messages can be deleted easily by clicking FROM and DELETE without having to read any of them. Save anything you wish to keep in DRAFT or in your own created KEEP folder, and it will stay in that folder until you delete it.
#37. Add the following at the end of your email if you do not want your receiver (Addressee) to broadcast or forward your email to someone else without your written consent: (Note: There is no guarantee that the Addressee will honor your request).
Sample 1: This document and/or attachment contains confidential and/or privileged information. The rights to privilege have not been waived. Copyright is owned by I. Lee (enter your name or company name) without whose written permission, none of this document may be excerpted, reprinted, or forwarded to anyone.
Sample 2: This message is intended only for the use of the addressee and may contain information that is privileged and confidential. If you are not the intended recipient or have received this communication in error, you are hereby notified that any unauthorized use or disclosure is strictly prohibited. Please notify the sender immediately and delete the original without making a copy or disclosing its contents.
Sample 2 (in French, for bilingual Canadian users): Le présent message s'adresse exclusivement à son destinataire et peut contenir des renseignements privilégiés et confidentiels. Si vous n'êtes pas le destinataire de ce document ou si vous l'avez reçu par erreur, vous êtes par la présente avisé qu'il est strictement interdit de le divulguer ou de l'utiliser sans autorisation. Veuillez en avertir l'expéditeur immédiatement et détruire le message original sans le copier ou en révéler le contenu.
Sample 3: The information transmitted in this electronic message is confidential. It is intended for the exclusive use of the person to whom it is addressed and may not otherwise be read, distributed, copied or disclosed.
Sample 4: Confidentiality Note: This message is intended only for the use of the named recipient(s) and may contain confidential and/or proprietary information. If you are not the intended recipient, please contact the sender and delete this message. Any unauthorized use of the information contained in this message is prohibited.
#38. Always print, or save on disk or hard drive, a copy of important email you have received or have sent to someone.
#39. When you send email messages using To: and Cc: (Carbon Copy) the names or email addresses will be visible to all recipients. If you use Bcc: (Blind Carbon Copy) the names or email addresses of the recipients will not be visible to either the To: or the Cc: recipients. If you want a record of the people to whom you have sent a Bcc: message, you will need to save or print the DRAFT before you hit SEND. Even if there are several people on your Bcc: list, each person can only view one name, the recipient himself or herself whose email address the message was sent to. The To: and Cc: names, however, remain visible to all.
#40. Bcc: is a very private way to send email messages. When you use Bcc: it will not allow that recipient to further forward other email addresses onto someone else since other Bcc: email addresses are not visible to the recipient.
#41. When forwarding an email message to someone, remove the original sender's email address unless it is the wish of the original sender that you forward his or her email address to your recipient along with the message.
#42. Don't add unnecessary clutter to the Internet by forwarding chain letters to show that you are a caring and loving person, or to bring luck to yourself and to 5, 10, 20 or more other people by email.
#43. Don't send free eCards accompanied with music, sentimental or spiritual messages, animated cartoons and the like to your friends and relatives as all their email addresses as well as yours may become readily available for sale to third parties without your knowledge or consent. Don't be surprised that you and your friends suddenly receive tons of spam mail shortly after sending or picking up an e-card.
#44. Spam is unsolicited commercial email that has become an extremely serious problem on the Internet. Learn about the new Canada's Anti-Spam Legislation effective July 1, 2014. "Canada's anti-spam legislation (CASL) is in place to protect Canadians while ensuring that businesses can continue to compete in the global marketplace. IF YOU USE ELECTRONIC CHANNELS TO PROMOTE OR MARKET YOUR ORGANIZATION, PRODUCTS OR SERVICES, CANADA'S NEW ANTI-SPAM LAW MAY AFFECT YOU. It is your duty to understand and comply with the law ... Fact: There are no automatic penalties. The CRTC has a range of enforcement tools available, from warnings to penalties (up to $1 million for individuals and $10 million for businesses)." See also Spam in the Virtual Library for more info and free downloads of anti-spam software.
#45. Learn to search effectively online as information on the WWW is not systematically organized.
#46. Set a time or item limit for research and try sticking to it.
#47. If you have a task to perform, don't allow cyber ads to distract you, stay focused on your task.
#48. Try not to become overly addicted to the Internet and ignore your loved ones in the process.
#49. Bookmark your favorite sites.
#50. Immediately print or save information that you find useful, for you may never see the same site again.
#51. Make backups of all data that you don't want to lose.
#52. Keep important CDs, DVDs, boot disks, rescue disks, tape backups, etc. readily available for emergency use.
#53. If your system is terribly fouled up, and you don't have a program that would sweep it clean and fix it for you, you may need to take the drastic step to format your entire hard drive and reinstall everything from scratch. Check out Tools for Webmasters for useful clean-up or fix-it tools, but use such software cautiously so as not to throw out the baby with the bath water by wiping out needed files along with the junk.
#54. Never delete important system files that you have no clue as to what they are being used for.
#55. Always use UNINSTALL instead of DELETE to get rid of unwanted programs if you have an option.
#56. To UNINSTALL or remove a program you don't want, go to Start - Settings - Control Panel. Click on Programs and Features and choose Uninstall a Program. Select a program from the list, then click "Uninstall". Depending on the operating system you use, the commands may be slightly different.
#57. Clean out the cache or close and exit the program after banking online, especially if you are using public computers. Do delete useless files and email messages regularly at your own computer.
#58. Every now and then CLEAN OUT all your cookies to eliminate offensive email or unwanted ads. The procedure to wipe out cookies may vary with different browsers. If using Internet Explorer, click on Tools, select Internet Options. Under Temporary Internet files, click on Delete Cookies box, click OK to Delete all cookies in the Temporary Internet Files folder. The cookies that you need and want will come back when you access those sites the next time.
#59. Be watchful of spyware residing in your computer often without your knowledge or consent. Such software violates your privacy, continuously uses memory on your computer when you are surfing, and adds to more clutter on the WWW. Spyware is generally used to track or trace all your Internet usage in detail and the information thus gathered is sent to the software developer. Such information may be sold to third parties or used for other purposes not to your liking.
#60. It is a good idea to install a reputable spyware detection and removal program on your computer. You can download for free a copy of AVG Free Anti-Virus - Free antivirus and anti-spyware, HouseCall from Trend Micro, a free online virus and spyware scanner, Spybot Search & Destroy, Ad-Aware, Spyware Blaster, or SUPERAntiSpyware, ">SUPERAntiSpyware. The purpose of anti-spyware software is to scan your computer system to detect any software components that you don't want or are not aware of their existence on your system, and to provide you with an option to remove these hidden cookies. See Security & Spyware for more free downloads of Spyware Removal programs.
#61. Check out Top 15 internet safety rules and what not to do online from Kaspersky, Online Scams from U.S. Norton. Free Tools, Apps, and Trials from TrendMicro. Trend Micro offers a range of free tools to protect your devices and help you manage your online activity.
● 10 secrets to uncovering which online reviews are fake from Market Watch, Dec 10, 2018.
#62. Be wary of using P2P Peer-to-Peer software. Info from Wikipedia, the free encyclopedia. Take note of Copyright Infringement Liability, Data Security, Spyware, Viruses, and other associated problems.
#63. Health comes first. Be kind to your body and make sure that it gets the proper exercise, nutrition, and rest that it deserves.
#64. At the first sign of eyestrain, fatigue, cramps, hunger or thirst - QUIT, or check out the following sites for consequences:
● How to Survive the Internet by Janet Williams, Seattle.
● Internet addiction disorder from Wikipedia, the free encyclopedia. "Internet addiction "disorder" (IAD), also known as problematic internet use or pathological internet use. It is a problematic compulsive use of the internet, particularly on social media, that impairs an individual's function over a prolonged period of time."
● Internet Addiction Test (IAT) - A test for online users to determine if you may be addicted to the Internet.
● Internet Addiction: The Emergence of a New Clinical Disorder - in PDF, 13 pages by Kimberly S. Young, University of Pittsburg, at Bradford.
● Internet Addiction: Symptoms, Evaluation, and Treatment by Kimberly S. Young.